Post : PBKDF2 (Password Based Key Derivation Function 2 Algorithm)
Title : PBKDF2 (Password Based Key Derivation Function 2 Algorithm)
PBKDF2 (Password Based Key Derivation Function 2 Algorithm)
What is PBKDF2?
PBKDF2 is used in WPA-2 and TrueCrypt. Its main focus is to produce a hashed version of a password and includes a salt to reduce the opportunity for a rainbow table attack.
The generalise format for PBKDF2 is:
DK = PBKDF2(PRF, Password, Salt, MInterations, dkLen)
Where PRF is a pseudorandom function of two parameters with output length hLen, Password is the pass phrase, Salt is the salt, MInterations is the number of interations, and dklen is the length of the derived hash.
PBKDF2 (Password-Based Key Derivation Function 2) is a key derivation function that is part of RSA Laboratories' Public-Key Cryptography Standards (PKCS) series, specifically PKCS #5 v2.0, also published as Internet Engineering Task Force's RFC 2898. It replaces an earlier standard, PBKDF1, which could only produce derived keys up to 160 bits long. It generally uses over 1,000 iterations in order to slow down the creation of the hash, so that it can overcome brute force attacks.
Often this is used to create an encryption key from a defined password, and where it is not possible to reverse the password from the hashed value. It is used in TrueCrypt to generate the key required to read the header information of the encrypted drive, and which stores the encryption keys.
Each hLen-bit block Ti of derived key DK, is computed as follows:
DK = T1 || T2 || ... || Tdklen/hlenThe function F is the xor (^) of c iterations of chained PRFs. The first iteration of PRF uses Password as the PRF key and Salt concatenated with i encoded as a big-endian 32-bit integer. (Note that i is a 1-based index.) Subsequent iterations of PRF use Password as the PRF key and the output of the previous PRF computation as the salt:
Ti = F(Password, Salt, c, i)
F(Password, Salt, c, i) = U1 ^ U2 ^ ... ^ Uc
where:
U1 = PRF(Password, Salt || INT_32_BE(i))
U2 = PRF(Password, U1)
...
Uc = PRF(Password, Uc-1)
In this post, we will share you some online tools which you can use to generate pbkdf2 password hash.
PBKDF2 Creation (Javascript)
var hmacSHA1 = function (key) {Here are the some examples
var hasher = new sjcl.misc.hmac(key, sjcl.hash.sha1);
this.encrypt = function () {
return hasher.encrypt.apply(hasher, arguments);
};
};
// Adapted from: http://stackoverflow.com/questions/3745666/
function hex2a(hex) {
var arr = [];
for (var i = 0, l = hex.length; i < l; i += 2) {
arr.push(String.fromCharCode(parseInt(hex.substr(i, 2), 16)));
}
return arr.join('');
}
// Default test
// 29EEE7AA9C0E9315:1000:3c46e7944864305b846ef32cd3f47655ecbc04f1c47617e606556ee2fb6d066f
// This will brick your browser when running with CryptoJS or Anandam...
// 972D41DD415CF92C:695525:468917399F0699634105DD618F26483BCEABF9ED
var iterations = 1000;
var password = 'password';
var hexSalt = '29EEE7AA9C0E9315';
var sjclSalt = sjcl.codec.hex.toBits(hexSalt);
var cryptoSalt = CryptoJS.enc.Hex.parse(hexSalt);
var keySizeBits = 256;
// SJCL
console.log('pbkdf2 SJCL', sjcl.codec.hex.fromBits(sjcl.misc.pbkdf2(password, sjclSalt, iterations, keySizeBits, hmacSHA1)));
// CryptoJS
console.log('pbkdf2 CryptoJS', CryptoJS.PBKDF2(password, cryptoSalt, {
keySize: keySizeBits / 32,
iterations: iterations
}).toString());
// Anandam
(new PBKDF2(password, hex2a(hexSalt), iterations, keySizeBits / 8)).deriveKey(function () {}, function (key) {
console.log('pbkdf2 Anandam', key);
});
Example 1
Message (or pass phrase): learn cryptography'
Salt (or SSID) (hex or ASCII): 52E7268B35D9294CE22A034BC3F4DD33
MInteration Count: 1000
DKlen: 20
(The salt will auto-detect if the value is an ASCII string or hex.)
Result would be like;
Hash (Hex): 9B3B6FEDC61989867858DC63A1EA5A07D605462
Hash (Base-64): CbO2/txhmJhnhY3GOh6loH1gVGI=Example 2
Password or message: cryptographer
Salt (or SSID) (hex or ASCII): 52E7268B35D9294CE22A034BC3F4DD33
MInteration Count: 2000
DKlen: 30
Result would be then;
Hash(Hex): 2C6178F81FA1E67AD91CB95A3A91663785E9F6D722B4D1321EAB6F53D2
Hash (Base-64): LGF4+B+h5nrZHLlaOpFmN4Xp9tcitNEyHqtvU9I=PBKDF2 online creation and calculator tools
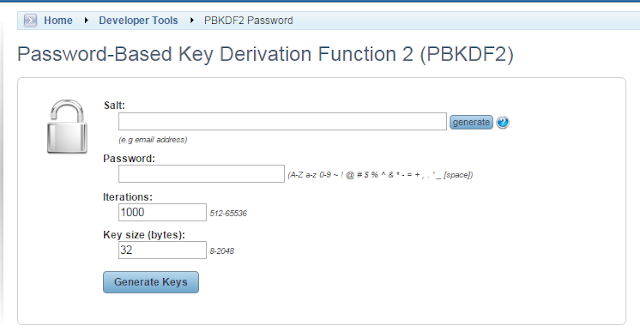
These are the tools which help users in generating the hash version of passwords and includes a salt to reduce the opportunity for a rainbow table attack.
The tool from available online tools, I like the most is NeuroTechnics tool. You can access this tool here.
This tool is developed by Neurotechnics Services. Neurotechnics provides services to industry of all shapes and sizes. From small (SOHO) businesses, to large business and international corporations. Neurotechnics provides services to industry of all shapes and sizes. From small (SOHO) businesses, to large business and international corporations.
Message: I hope that you have enjoyed 'PBKDF2 (Password Based Key Derivation Function 2 Algorithm)' article. However, if you want me to deliver more items, then please share my post. You can use Social Sharing Widget provided at the end of every post. After all, Sharing is Caring!
That is the article of PBKDF2 (Password Based Key Derivation Function 2 Algorithm)
make a blog website free
Here Come New Ideas for how do you start your own website for free PBKDF2 (Password Based Key Derivation Function 2 Algorithm), I hope my article give you benefit for you. Make a blog website free, how do you start your own website for free.

0 Response to "PBKDF2 (Password Based Key Derivation Function 2 Algorithm)"
Post a Comment